DNSSEC & DANE
Today, I spent some time rolling out DNSSEC for some of my zones to enable clients to verify DNS responses from my nameservers. I also added TLSA records (see RFC 6698) for some domains and for my mail server to provide an additional indication that the TLS certificates sent to the client come from me.
To benefit from DNSSEC and DANE in daily internet life, you can install the DNSSEC/TLSA Validator add-on in your Browser. It will provide you with two additional indicators beside your address bar. It will give you information on
- Whether the domain name of the URL you are visiting is secured by DNSSEC.
- Whether there is a TLSA record available for the Domain, and if the TLSA record corresponds to the TLS certificate or public key of the web server.
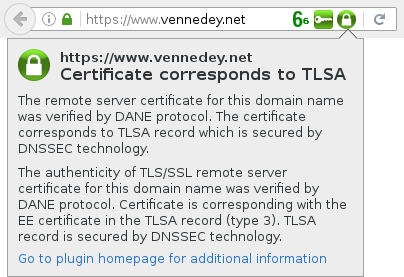
In the extension's preferences you can enable the option “Cancel HTTPS connection when TLSA validation fails”. This might protect you from a man-in-the-middle attack even if the attacker was able to provide a certificate of the domain from a trusted authority.
If you like to secure your zone with DNSSEC, you first have to find out if your registrar allows you to upload your KSK to the registry. Unfortunately, this is not common nowadays. If you don't find an option in the registrar's control panel, open a support ticket and ask for it.
Then, you need to generate your keys, sign your zones and supply TLSA records for your certificates. Since the keys used along with DNSSEC are comparatively short, you are well-advised to rotate them regularly.
Here are some recommendations on how to achieve all this with bind9 and its „inline signing“ feature.